Securing your RDP Ports

Are you using or planning to use Remote Desktop Protocol (RDP) but feeling a bit lost when it comes to ports and the security measures involved?
What's an RDP Port, anyway?
Think of an RDP port as a special doorway for your remote connection. By default, Windows uses port 3389 for RDP. This port allows your local computer to chat with the remote one, making that magical remote desktop experience possible.
TCP, UDP, and RDP - The key protocols behind Remote Access
Before diving deeper, let’s clarify how these protocols work,
TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are the backbone of internet communication. TCP ensures that data packets are sent and received in the correct order, with error-checking in place—think of it as a reliable courier service that guarantees delivery. On the other hand, UDP is faster but less reliable, sending packets without verifying their arrival—like a quick message sent without confirmation.
RDP (Remote Desktop Protocol) leverages both TCP and UDP. It primarily uses TCP for stable, reliable connections, but can switch to UDP for faster performance when low latency is needed. RDP goes beyond just transporting data; it also adds encryption and other layers of security to protect the remote desktop connection.
The security risk of default ports
Cybercriminals frequently target the default RDP port 3389, making it a significant security vulnerability. Using the default port is akin to leaving your front door unlocked in a high-crime area. Changing your RDP port is a simple yet effective security measure, comparable to hiding your entrance where intruders are less likely to look.
While Port 3389 is the standard for RDP connections, using these RDP port alternatives can enhance security,
- 3390 and above: These are commonly used alternatives to the default port, offering better protection from attacks targeting port 3389.
- Custom ports: For even greater security, pick a unique port number above 1024. This helps reduce exposure to automated attacks while staying within a safe range for system performance.
Changing your RDP port: A step-by-step guide
Ready to secure your connection?
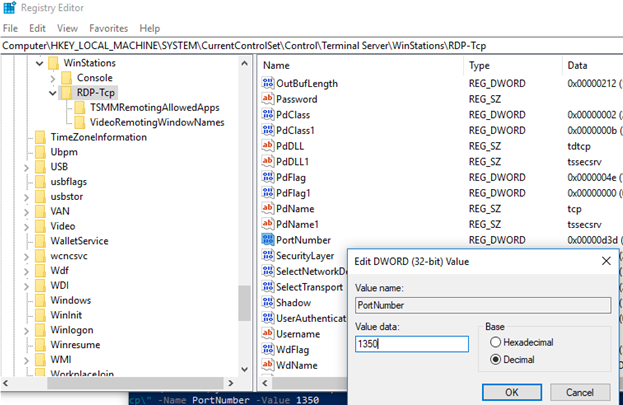
Open Registry Editor
Press WIN+R, type regedit, and press Enter.
Navigate to Key
Go to HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp.
Change Port
Double-click PortNumber, select Decimal, and input a new port (e.g., 74009).
Check Port Number
Run in PowerShell to verify
Adjust Firewall
Restart RDP Services
Use net stop termservice && net start termservice in Command Prompt.
Pro Tip: Document your changes for future reference and troubleshooting.
Uh-oh, connection problems? Let's troubleshoot
Changed your port but can't connect? Check these common culprits:
- Firewall settings: Make sure it's not blocking your new port
- Port forwarding: If connecting from outside your network, this needs to be set up correctly
- Double-check your changes: A tiny typo can cause big headaches
Which leads a segue into another concerning issue.
Time-consuming aspects of RDP configuration
Setting up RDP can sometimes feel like solving a long winded maze. Here are the tricky bits that often eat up time:
- Security Setup: Changing ports, configuring firewalls, implementing SSL certificates.
- Network Configuration: Wrangling NAT, port forwarding, and VPN integration.
- User Management: Creating accounts and setting up multi-factor authentication.
- Performance Tuning: Optimising for various network conditions and tweaking settings.
- Ongoing Maintenance: Regular security check-ups and patching.
- Troubleshooting: Solving connectivity puzzles and performance hiccups.
- Scaling: Adding new servers and balancing the load.
Each of these can turn into a time-consuming quest consuming hours or even days of your IT resources, depending on the complexity of your environment.
Using RDP within Neverinstall
While understanding RDP ports is valuable, wouldn't it be great if you could skip all the complicated setup? That's where Neverinstall cloud PCs come in, shifting how distributed teams access secure Remote Windows environments.

Neverinstall: RDP Windows streaming without the headaches
Neverinstall leverages RDP technology but removes the usual complications.
- One-Click Configuration
Simplify port access and team-wide reconfiguration with a single module. - Instant Secure Remote Access
Get immediate access to controlled Windows environments, bypassing lengthy RDP setup. - Robust Security
Enjoy built-in protections including static IPs, granular access controls, DNS filtering, and compliance certifications (GDPR, SOC II, HIPAA/PCI-DSS ready). - Streamlined Admin Control
Manage organizational permissions and access through a user-friendly dashboard, simplifying workforce management. - Consistent Performance
Experience smooth, high-performance Windows virtual desktop access anywhere, thanks to adaptive streaming technology, optimized bandwidth usage, and built-in load balancing.
How Neverinstall works
- Team members log in through a web browser – no client software required.
- Behind the scenes, Neverinstall uses optimised RDP connections for a seamless and intuitive native-feel experience.
- IT teams can focus on productivity rather than playing RDP whack-a-mole with issues.
- Organisations cut their TCO by up to 52% due to the lesser dependence on IT specialists, reduced server usage, and better control over your cloud and infrastructure costs.
By abstracting away the complexities of RDP, Neverinstall allows distributed teams to enjoy the benefits of remote Windows access without the traditional hurdles.
Wrapping up: Why RDP ports matter (and when they don't)
Understanding RDP ports is crucial for anyone managing their own remote desktop setup. With a few tweaks, you can significantly boost your security and potentially improve performance.
In some scenarios, changing the RDP port might not significantly enhance security or performance. For example:
Behind a VPN
If your system is behind a properly configured VPN, the RDP port is already shielded from public exposure.
Restricted Network Access
In a tightly controlled corporate environment where access is limited to specific IP addresses or uses strong multi-factor authentication, the need for changing the port is reduced.
Firewalls and Security Layers
When robust firewall rules or network security protocols are in place, changing the RDP port becomes less critical.
However, solutions like Neverinstall show that it's possible to enjoy secure, high-performance remote desktops without diving into the technical complexities of RDP configuration.
Ready to level up your Remote Desktop game?
Whether you're a hands-on tech enthusiast who loves optimising RDP settings or you're looking for a hassle-free solution, there's an option for you.
Give Neverinstall a spin with a tailored trial run for your team– your productivity (and your IT team) might thank you!





