Choosing the right privacy tool
Cloud browsers, Virtual Private Networks (VPNs), and Cloud PCs are widely used solutions for maintaining privacy and gaining more flexbility with your security posture. But which one best suits your needs at this moment? Let's figure it out.
Understanding the basics
What are Cloud Browsers?
- Run on remote servers, not your device
- Stream rendered content back to you
- Create a barrier between your device and websites
How do VPNs (Virtual Private Networks) work?
- Encrypt your internet traffic
- Route it through remote servers
- Mask your IP address and location
What about Cloud PCs?
- Provide a full desktop environment in the cloud
- Accessible from any device with internet
- Run all applications and processes remotely
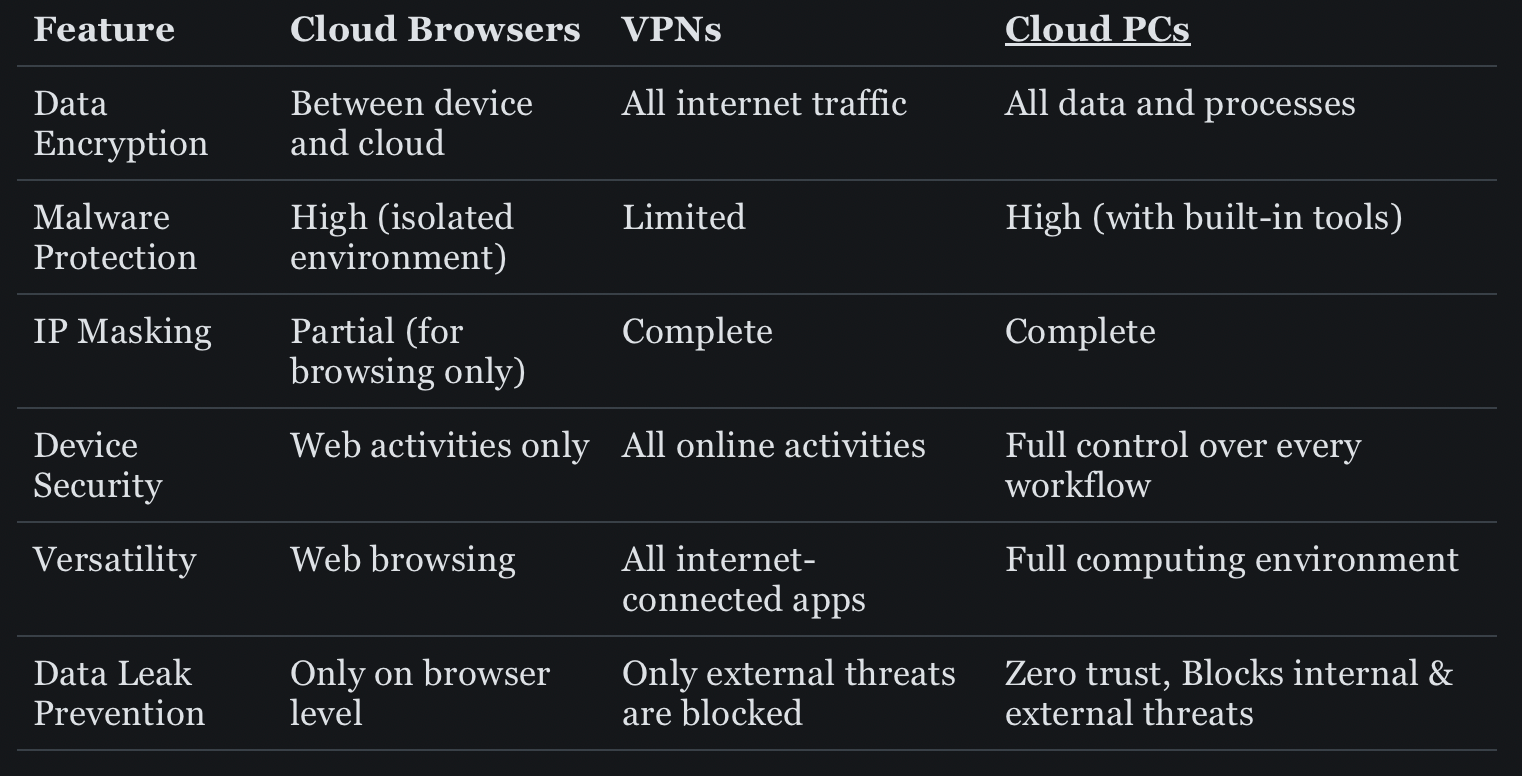
Pros and cons
Cloud Browsers
✅ Excellent malware protection
✅ Reduced local resource usage
❌ Limited to web activities
❌ Potential privacy concerns with provider
VPNs
✅ Comprehensive online privacy
✅ Works with all internet-connected apps
❌ Potential speed reduction
❌ No inherent malware protection
Cloud PCs
✅ Completely sandboxed environment protection
✅ Access from any device with controls over apps, uploads, sharing & filtered URLs
✅ Data recovery & role based access to pretected data
❌ Relatively higher cost
Choosing the right privacy tool
Each technology has its strengths for specific use cases:
- VPNs: Ideal for privacy-focused users and travelers.
- Strengths: IP masking, encryption for all online activities.
- Best for: Accessing geo-restricted content, securing public Wi-Fi connections.
- Cloud Browsers: Excellent for casual users concerned about web-based threats.
- Strengths: Malware isolation, reduced local resource usage.
- Best for: Safe browsing on potentially risky websites, lightweight security solution.
- Cloud PCs: Comprehensive solution for businesses and power users.
- Strengths: Full environment security, centralized management, scalability.
- Best for: Remote work, handling sensitive data, compliance-heavy industries.
While VPNs and cloud browsers excel in specific scenarios, cloud PCs offer a more holistic approach. They provide:
- Integrated security features (built-in firewalls, antivirus)
- Consistent secure environment across devices
- Easier compliance management with HIPAA, GDPR, SOC II, PCI-DSS, etc.
- Potential for better long-term ROI through reduced IT overhead and scalability
- Native local device experience with scalable hardware in a granularly controlled environment.
Consider your primary security needs, technical comfort, and long-term goals when choosing. For comprehensive protection that goes beyond browsing or network security, cloud PCs present a compelling option.
Security Concerns to Keep in Mind
- Data Logging: Some providers may log user data despite claims otherwise.
- Encryption Strength: Ensure the solution uses strong, up-to-date encryption protocols.
- Provider Trustworthiness: Research the reputation and practices of your chosen provider.
- Legal Jurisdictions: Be aware of data retention laws in the provider's country.
The Bottom Line
There's no one-size-fits-all solution in this cybersecurity maze. Your choice depends on your specific needs, technical comfort, and budget. For maximum security, consider combining approaches – for instance, using a cloud browser through a VPN connection.
But hey, why not consider Neverinstall?
We build simplified cloud PCs and virtual desktop solutions for businesses that want a distinctive edge with their workspaces.
A big problem in this space is that alternatives like Azure Virtual Desktop, Windows 365, AWS Workspaces, or Citrix come with heavy manuals for each and every configuration. You're looking at a rather steep technical learning curve, and additional costs for every component you stack up for your infrastructure and interface needs.
With Neverinstall, you can forget about the convenience headaches and the overhead of a dedicated IT team. We ensure quick DaaS and VDI setups for agile teams, giving instant access to flexible cloud workspaces where you know your enterprise data will remain secure.
Remember, while these tools significantly enhance your online security, they're not infallible. Maintain good cybersecurity practices regardless of the solution you choose.
Stay safe out there!
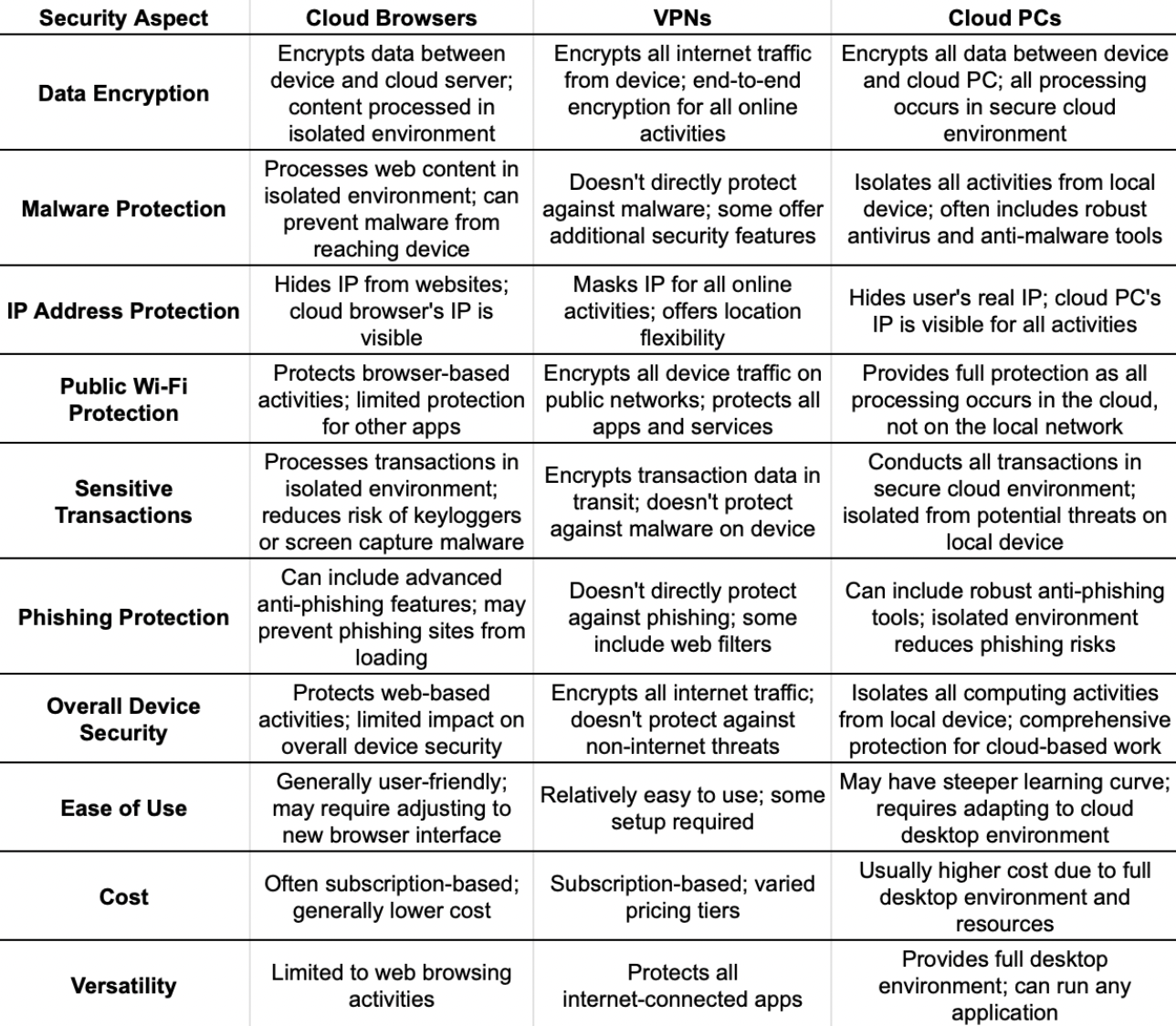
Comprehensive security overview of Cloud Browsers, VPNs and Cloud PCs






Join the conversation.