Active Directory (AD), including Microsoft Active Directory, is a critical infrastructure service developed by Microsoft, designed to manage users, devices, and resources in a networked environment. At its core, AD provides centralised authentication and authorisation through features like Active Directory Users and Computers and Group Policy Management, ensuring that only authorised users can access the resources they need while keeping unauthorised users out. It simplifies security and management.
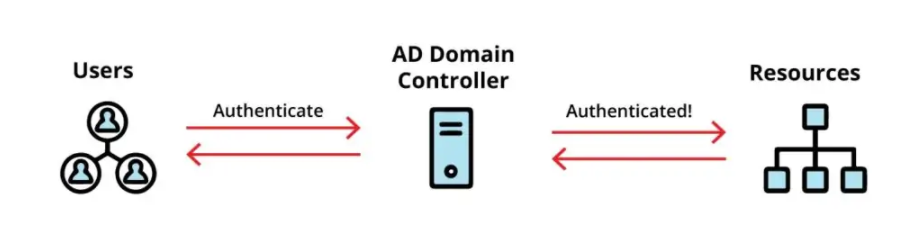
The Basics of Active Directory
Active Directory operates on a hierarchical structure of objects, which include users, computers, and groups, organised within Active Directory Domains, trees, and forests.
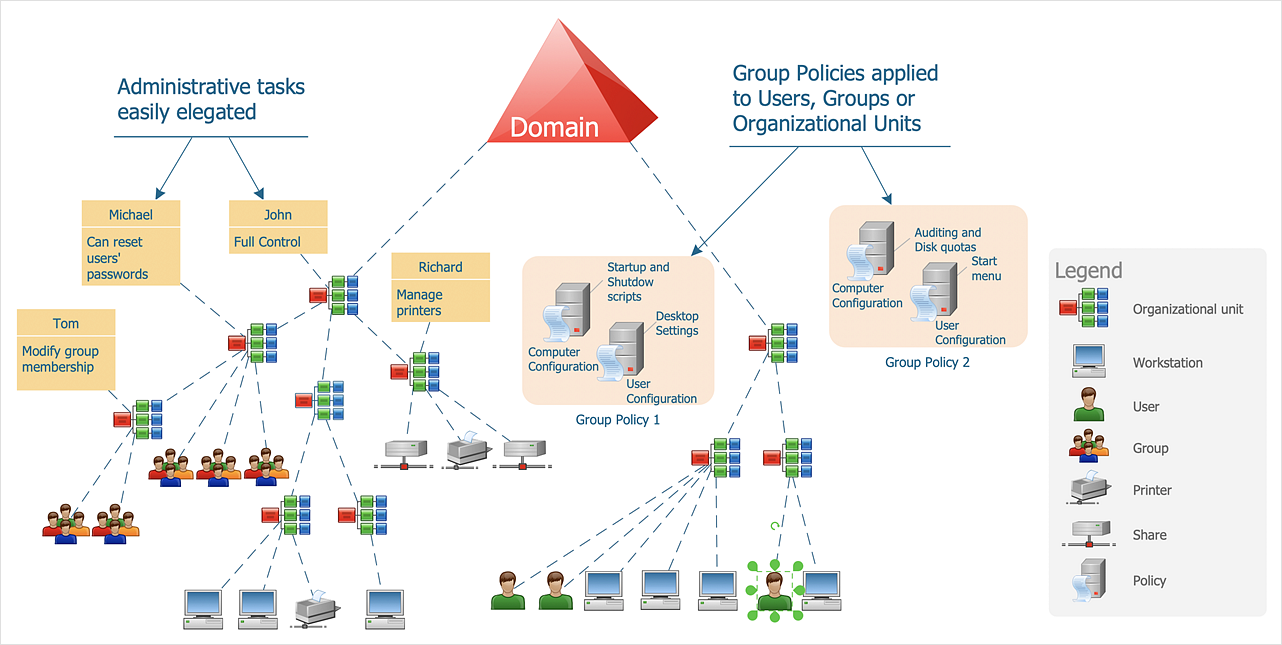
The hierarchical structure of Active Directory
Objects are created such as,
- Users: Individual accounts for employees and other authorised personnel.
- Computers: Network-connected devices managed by AD.
- Groups: Collections of users or computers for easier management.
These objects are organised within Active Directory Domains, trees, and forests.
Domain Controllers (DCs) are servers that host AD and manage security policies for all computers in the domain.
Organisational Units (OUs) are containers within a domain that can hold users, groups, and computers, allowing for granular management and delegation.
Group Policy is a feature that allows administrators to implement specific configurations for users and computers, enhancing security and streamlining operations.
LDAP vs Active Directory
When deciding between Lightweight Directory Access Protocol (LDAP) and Active Directory (AD), small businesses need to consider their specific needs and existing infrastructure.
LDAP (Lightweight Directory Access Protocol)
• Open-source and cross-platform compatible
• Highly customizable, but requires more technical expertise
• Suitable for simpler directory needs and diverse IT environments
Active Directory (AD)
• Seamless integration with Microsoft products
• Comprehensive features (for group and user management)
• Scalable from small to large organisations
• Better suited for Windows-centric environments and cloud PC integration
Decision factors here will possibly include the following questions you would have to ask yourself,
- Existing infrastructure: Microsoft-heavy or diverse?
- Technical expertise: Adequate in-house capabilities for customisations?
- Growth plans: Is there a need for scalability?
- Feature requirements: Is your need a basic directory or comprehensive management?
For Microsoft-centric small businesses with growth plans, AD often proves more beneficial. LDAP may be preferable for those with diverse platforms and simpler needs.
Why Active Directory Integration Save Small Businesses
For small businesses, the necessity of a robust, secure, and scalable system like Active Directory cannot be overstated.
Centralised Management
AD allows small businesses to manage all network resources from a single point of control. This reduces administrative overhead, enabling IT staff to implement policies, manage permissions, and maintain security with ease.
Enhanced Security with Active Directory
With Active Directory Security Best Practices, small businesses can enforce strong security policies, such as multi-factor authentication (MFA) and Active Directory Password Policies, protecting sensitive data from breaches and unauthorised access.
Compliance
Many industries have strict regulatory requirements. Active Directory Auditing helps small businesses comply with these regulations by providing detailed logging and auditing capabilities.
Integrating your Active Directory with Neverinstall
Neverinstall is a modern web-based VDI/DaaS solution that allows any team to access Linux and Windows virtual desktop workspaces in an instant, enhancing the way small businesses access hardware and controlled virtual environments. By integrating your AD on Neverinstall, businesses can enjoy several added benefits,
Remote access simplified
Neverinstall allows users to access their desktop environments and applications from anywhere, securely. This flexibility is crucial in today’s remote and hybrid work environments, ensuring that employees can stay productive without compromising security. Neverinstall's custom protocol also optimises for your network speed for consistent performance.
Instant Cloud PC deployment
Neverinstall also offers instant deployment of your workspaces,compared to the hefty timelines associated with the alternatives. Get your workspace ready-to-go with pre-configured apps and security policies that can be tailored for your team.
Flexible infrastructure
By leveraging cloud PCs on any infrastructure of your choice, Neverinstall CloudLink reduces the need for expensive on-premises hardware. This is especially advantageous for small businesses that need to keep costs low while maintaining high performance. Cloud PCs offer the flexibility to scale infrastructure as needed without significant upfront investment, and Neverinstall keeps your cloud agnostic flexibility intact.
Seamless integration with Active Directory
Neverinstall integrates smoothly with Active Directory (AD), enabling centralised management of users and resources across both on-premises and cloud environments.
Enhanced Security
Security is further bolstered by Neverinstall’s advanced encryption and isolation techniques, ensuring that data remains secure in transit and at rest, regardless of where it’s accessed from. Neverinstall is SOC II and GDPR compliant, while it can also help your team make the case for your compliance whether it's PCI-DSS, HIPAA or more.
Advanced scalability & intuitive admin console
Neverinstall’s cloud-based model means that businesses can easily scale their operations without the technical expertise. Whether you’re adding new users, deploying additional applications, or expanding your use of cloud PCs, it can be done quickly and without the need for significant investment in new hardware. The console has been thoroughly optimised for a reduced IT expertise dependency, and less intensive tasks, which means your scalability lies entirely in your fingertips.
Looking for more tips on handling your AD better?
Secure Privileged Accounts with Active Directory
Securing privileged accounts in Active Directory is crucial to maintaining a secure environment. Here are some tips to help you get started.
Renaming Administrator Accounts
Strongly secure domain administrator accounts by renaming them from the default “administrator,” implementing strong Active Directory Password Policies, and requiring multi-factor authentication (MFA) for authentication.
Limit the Use of Privileged Accounts
Limit the use of highly privileged accounts and implement the principle of least privilege (PoLP) to grant users only the permissions they need.
Audit Administrative Accounts Regularly
Regularly audit administrative accounts to ensure they are being used appropriately.
Monitoring Active Directory for Signs of Compromise
Effective monitoring of Active Directory is essential to detect potential security breaches early.
Monitor Privileged Groups
Monitor for changes to privileged groups like Domain Admins, Enterprise Admins, and Schema Admins.
Track Anomalies
Look for spikes in bad password attempts, locked-out accounts, and disabled or removed antivirus software.
Review Privileged Account Activities
Review all activities performed by privileged accounts, logon/logoff events, and use of local administrator accounts.
Use Log Analyzer Tools
Use a log analyzer tool to quickly spot suspicious activity and generate reports.
Implementing Strict Password Policies in Active Directory
Implementing strict Active Directory Password Policies is a simple yet effective way to protect your environment.
Use Passphrases
Use passphrases instead of traditional passwords for better security.
Enforce Password Length
Require a minimum password length of at least 14 characters.
Prevent Reuse of Old Passwords
Enforce password history to prevent the reuse of old passwords.
Require Multi-Factor Authentication
Implement multi-factor authentication (MFA) for added security.
Keeping Systems Patched and Updated through AD
Regular patching and updates are crucial to protect against vulnerabilities in Active Directory.
Patch Known Vulnerabilities Quickly
Move quickly to patch known Active Directory vulnerabilities.
Regular Scans
Scan for and remediate vulnerabilities at least monthly, prioritizing high-risk issues.
Update Software
Identify and address any outdated or unsupported software.
Securing Domain Controllers in Active Directory
Domain Controllers (DCs) are the backbone of Active Directory, and their security is paramount.
Physical Security
Keep domain controllers physically secure in data centers and branch offices.
Enforce Security Baselines
Configure security baselines using built-in tools and enforce them with Group Policy Objects (GPOs).
Monitor for Attacks
Regularly monitor domain controllers for signs of attack or compromise.
Auditing Active Directory Changes
Auditing AD changes is essential to detect and respond to unauthorised changes.
Enable Auditing
Enable auditing of important events like account creations, deletions, and modifications.
Monitor Suspicious Changes
Monitor for suspicious changes to group memberships, user rights, and security policies.
Regularly Review Logs
Regularly review audit logs for any anomalous activity.
Conclusion
By implementing these Active Directory security best practices, small businesses can significantly reduce the risk of compromise and better protect their critical systems and data. Regular monitoring, patching, and auditing are essential to maintaining a secure AD environment.
With the additional integration of Active Directory on tools like Neverinstall, including cloud PCs, businesses can further enhance their security posture, prevent data loss, ensuring robust, scalable, and secure operations in both on-premises and cloud environments.







Join the conversation.